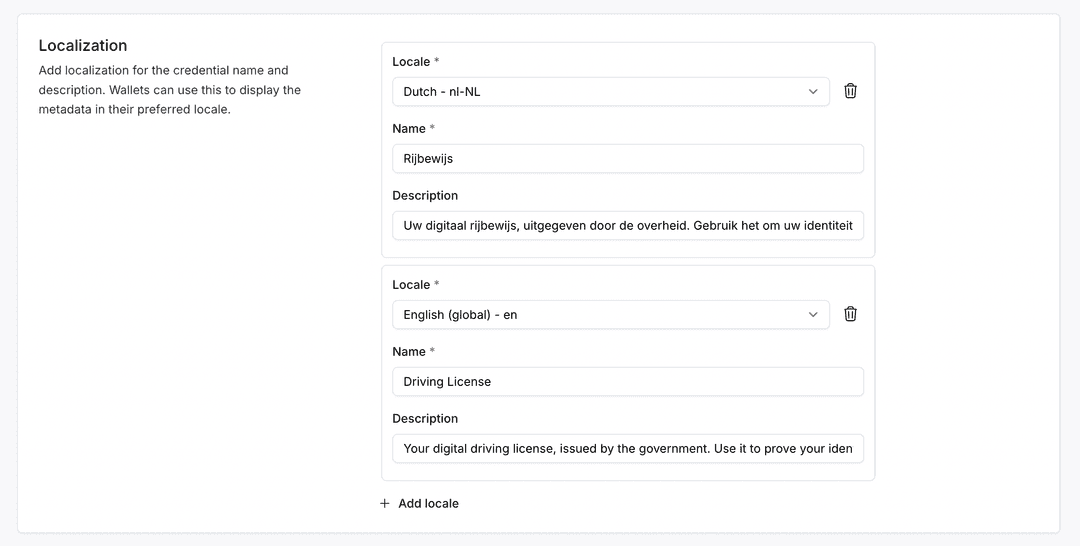
Paradym now supports full localization for credential templates, attributes, and issuer/verifier profiles. You can provide translations in multiple locales to improve the user experience across different regions.
With localization support, you can translate:
- Credential template names and descriptions: Display credential types in the user's preferred language (e.g., "University Degree" / "Universitair Diploma")
- Credential attributes: Translate individual claim names (e.g., "First Name" / "Voornaam")
- Issuer and verifier display names: Show your organization's name in multiple languages
All localized metadata is automatically included in OpenID4VCI issuer and OpenID4VP verifier metadata, allowing wallets to detect and display content in the user's language without additional configuration.
Localization is supported for SD-JWT VC and mDoc credentials. You can configure a default locale on your profile, and add translations for over 80 supported languages using BCP47 language tags (e.g., "nl-NL", "de-DE", "fr-FR").
To start using localization, check out the Localization documentation or configure it through the API or dashboard when creating or updating credential templates and profiles.